A fast, easy-to-use, yet powerful tool
for automated mobile app security testing
No code,
plug and play analysis
To get started, you only need to upload your app to the system. No need to write any scripts or analysis rules, just select the file you need. The standard scan takes 5 minutes.
Easy test automation
The comprehensive testing approach
Built-in Remediation support
Mobix Platform
Reduce time-to-market with automated application security testing on the Mobix platform. Get test results quickly, no need to wait for the next pentest.
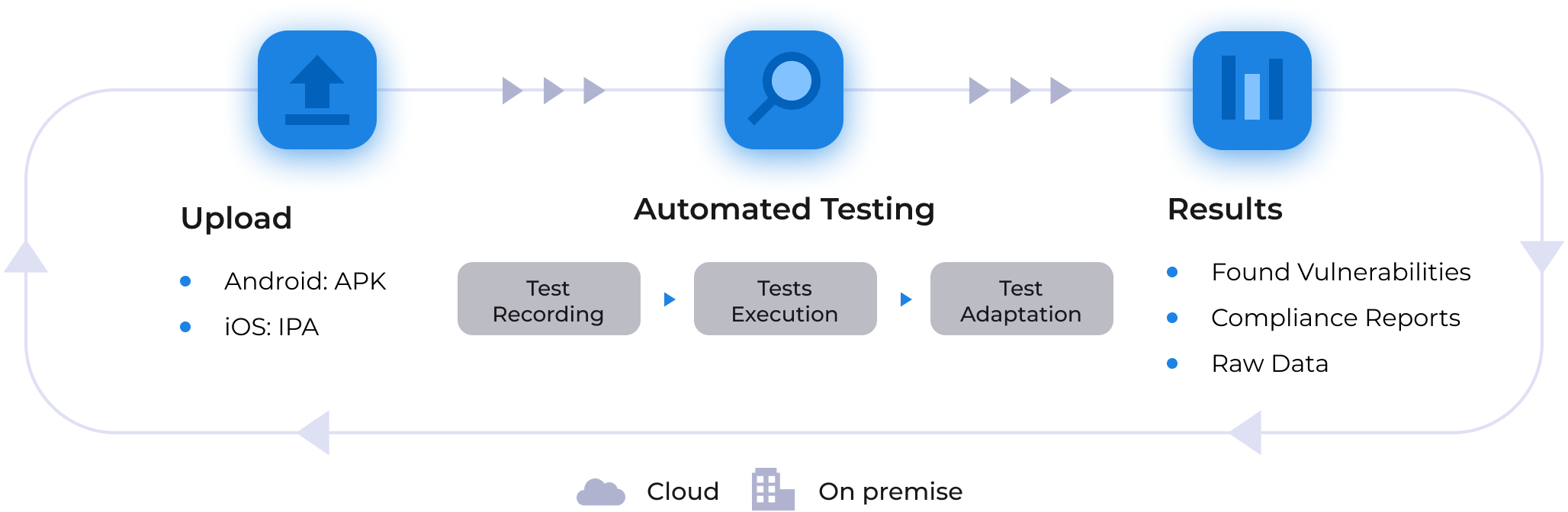
Mobix platform features
- Finding 60+ vulnerability types
- Android and iOS applications
- Dynamic Application Security Testing (DAST)
- Byte Code Analysis (BCA)
- Interactive Application Security Testing (IAST)
- Application Programming Interface Security Testing (API ST)
- Validation according to OWASP Mobile Top 10, SANS25, CVE, CWE lists
- Validation according to regulatory and industrial standards: OWASP MASVS, OWASP Mobile Top-10, PCI DSS, GDPR, HIPPA, etc.
- Creation of automated tests using AI based technology
- Collection of application data for further analysis
- Vulnerability descriptions with the detailed remediation guide
- Simple modification of security analysis rules for each application
- Testing applications in multiple threads on different OS versions with the ability to manage a queue of apps
- Integration into continuous development process (DevOps)
- A simple and intuitive UI that allows testers to identify vulnerabilities without any programming knowledge.
The only platform that enables full-scaled automation of mobile application security testing
Test recording
Mobix records all user actions and the responses of the application. Based on this record, Mobix creates auto-tests.
Test execution
Mobix automatically reproduces recorded auto-tests. Each time the application UI changes, Mobix analyzes if the tests are correct and will lead to the same results.
Test adaptation
Using machine learning and deep integration with the mobile OS, Mobix automatically adapts auto-tests to changing UI elements.
Improve the quality of application security testing
Automate security testing without coding skills.
First of all, Mobix is made for security analysts. To record a test case they do not need to write scripts. The UI is intuitive and user-friendly allowing fast configuration and automation of test cases.
Add and modify scanning rules to find specific bugs faster.
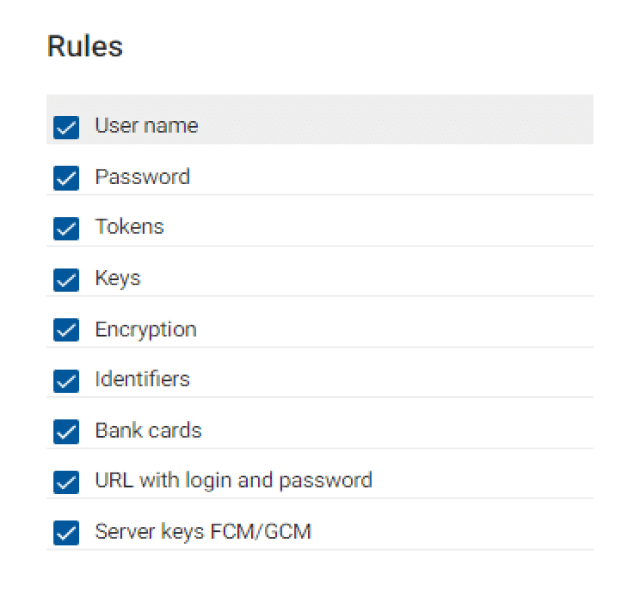
You may modify and add your own scanning rules for each test. This helps in finding specific vulnerabilities and reduce false positive and false negative results.
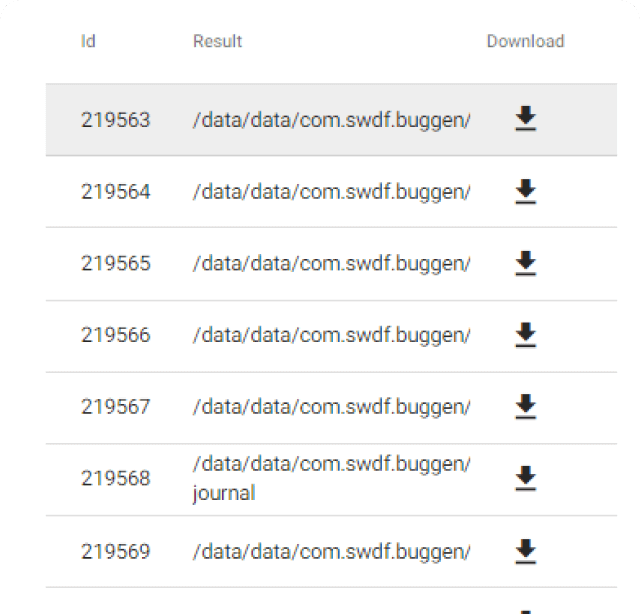
After scan completed, Mobix provides you with structured application performance data. This data may help to shorten manual discovery of sophisticated vulnerabilities.
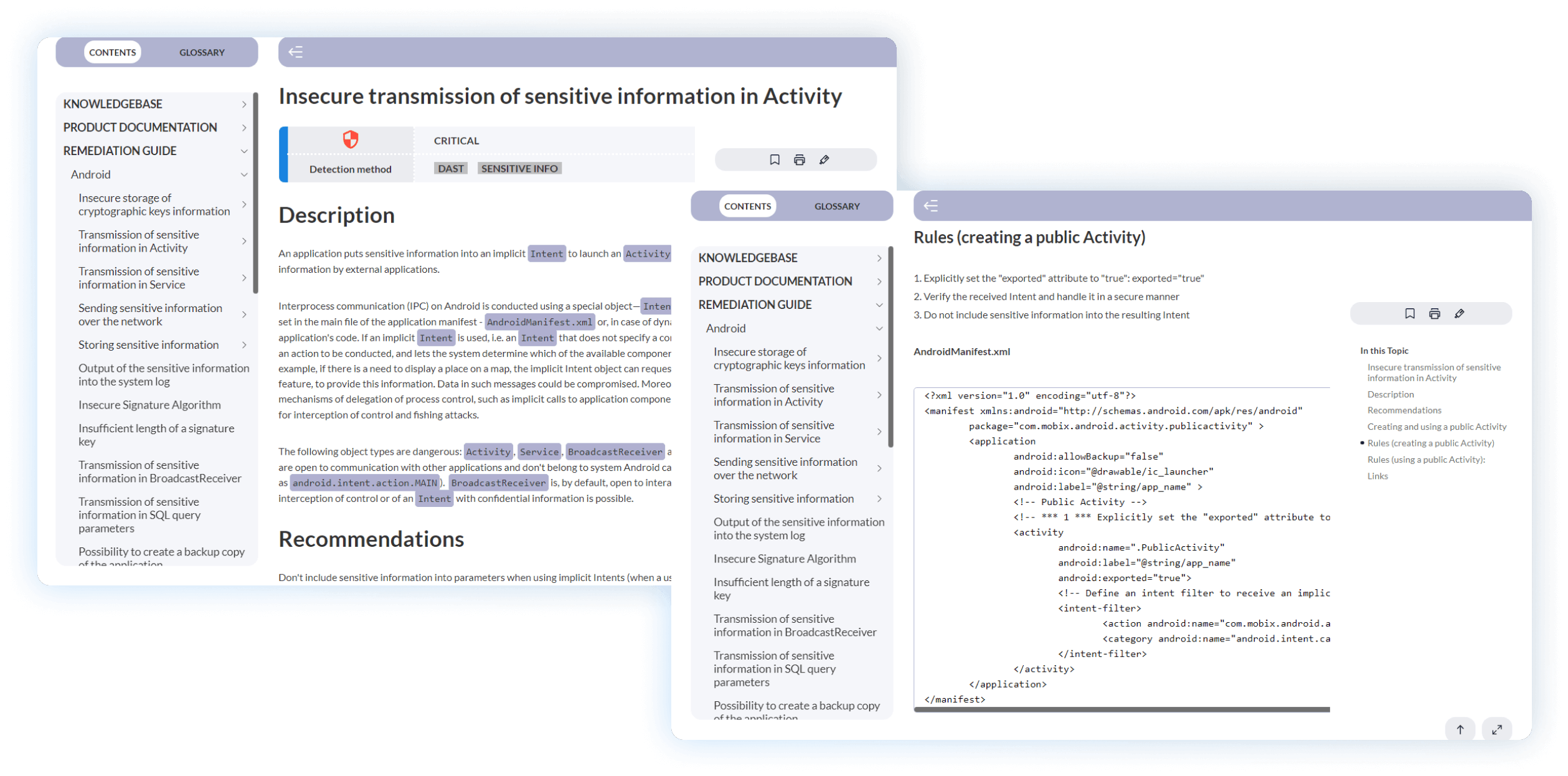
Detailed remediation guide
Security analysts are given detailed descriptions of any vulnerabilities discovered and potential data leakages, and specific recommendations on how to fix them.
Integration capabilities
Mobix is fully ready for integration with DevOps tools in the most commonly used CI/CD frameworks in the Android and iOS mobile industry, Defect Tracking Systems, Distribution Systems, Application Security Orchestration and Correlation (ASOC).




Distribution systems:






Open API (including JSON API and CLI) provides powerful integration and automation capabilities.
Regulatory Compliance

Mobix reports in accordance with industry classifiers:
- MASVS
- OWASP Mobile Top 10
And with the vulnerability classification adopted in:
- PCI DSS
- OWASP
- HIPAA
- CWE/SANS Top 25
Deployment Options
On-premise installation
Allows to install the solution within software development perimeter of delivery organization, which is important for regulated industries and large enterprises.
SaaS
The SaaS version is designed for small and midsize businesses seeking lower upfront costs, system stability and ease of access.
Implementation Results
reduction by
%
%
%
Case Study

Vivid Money
- Vivid Money, one of the leading neo banks in the EU, was seeking to improve its cybersecurity posture for its mobile banking application, a critical component to its business model.
- The challenges included a lot of manual labor, sub-optimal coverage, and time-to-market delays. Manual checks were labor-intensive and took a significant amount of time.
- Vivid Money was looking for automation with full testing coverage, integration with a bug tracking system, CI/CD systems, and an intuitive UI. Also, compliance checks with OWASP MASVS standards are crucial within the banking business.

“Before Mobix, manual mobile security testing involved two full working days per week of the application security engineer plus extra 12 man-hours of Android and iOS developers weekly. This seriously affected the speed of delivery.
With Mobix situation has been changed dramatically: the security testing process is now fully automated. We get results faster. Security testing is no longer a blocking factor for releases and our Time-to-Market has improved significantly.”
Pricing
(billed annually)
1 User
No Integrations
Deployment: Cloud
Automated Tests
Supported Standards:
OWASP Mobile Top 10
SANS25
CVE
CWE OWASP MASVS
PCI DSS
GDPR
HIPPA
Learn more
(billed annually)
1-6 Applications
Unlimited Users
All Integrations + Platform API
Deployment: Cloud
Automated Tests
Supported Standards:
OWASP Mobile Top 10
SANS25
CVE
CWE OWASP MASVS
PCI DSS
GDPR
HIPPA
Learn more
Enterprise DevSecOps-ready solution for secure software engineering process. Ideal for teams with continuous releases of mobile applications.
Custom Terms
Unlimited Applications
Unlimited Users
All Integrations + Platform API
Deployment: Cloud & On-premise
Automated Tests
Supported Standards:
OWASP Mobile Top 10
SANS25
CVE
CWE OWASP MASVS
PCI DSS
GDPR
HIPPA
Learn more
